Azure Cloud Security
Introduction
In this project, I designed and implemented a highly available web server for XCorp’s Red Team to use for testing and training. This solution ensures security, scalability, and resilience in an Azure cloud environment. In this post, I will explain how I set up a secure cloud infrastructure, automated deployment using Ansible, and configured a load balancer for high availability.
About Ansible
Ansible is an open-source automation tool used for configuration management, application deployment, and task automation. I choose Ansible as it automates server set up using playbooks that ensure consistency as well as reducing human errors. It is also easily scalable incase XCorp adds more web servers in the future.
Step 1: Setting Up the Cloud Infrastructure
I first created a Resource Group in Azure, which contained all the cloud resources required for this setup.
Configuring the Virtual Network (VNet) and Network Security Group (NSG)
Next, I created a Virtual Network (VNet) with sufficient capacity to accommodate current and future Red Team resources. Then I deployed a Network Security Group (NSG) with an inbound rule that blocks all traffic by default.
Step 2: Deploying Virtual Machines
My first VM was a JumpBox virtual machine inside the VNet to act as a secure access point. (Name: JumpBoxProvisioner). I restricted SSH access to the current IP address only as well as installed Docker on the JumpBox to run containers securely.
Web VMs (DVWA Deployment)
Next I created two web VMs named Web-1 and Web-2. I used a SSH key for secure remote access and configured the JumpBox to access these machines internally.
Step 3: Configuring Ansible for Automated Deployment
I used an Ansible container to automate the installation of Docker and the Damn Vulnerable Web Application (DVWA) on both the web VMs.
Step 4: Setting Up Load Balancing and High Availability
I deployed an Azure Load Balancer to distribute traffic evenly across Web-1 and Web-2. Once configured, I adjusted security group rules to allow port 80 traffic from single IP address only.
I added both Web-1 and Web-2 to the backend pool of the load balancer to test redundency. This test was done by shutting down one of the VMs. I was able to verify that the DVWA site remained accessible.
Network Diagram
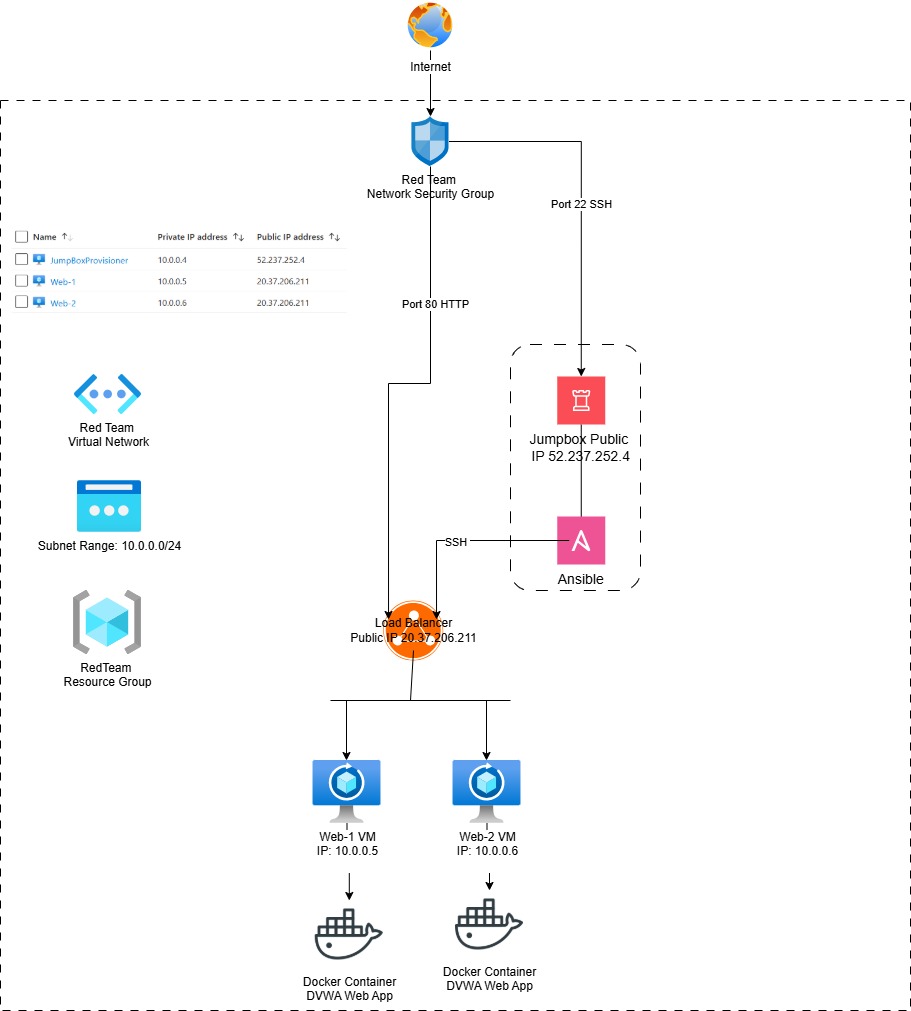
Conclusion
This project was designed to provide XCorp’s Red Team with a secure, highly available cloud-based testing environment. By leveraging Azure’s cloud infrastructure, I built a segmented, controlled environment that allows security assessments without unnecessary exposure. This setup mirrors real-world enterprise environments, where security, scalability, and reliability are essential.